Best ways to protect Research Data

How to protect research data from unauthorized access, sharing, editing, copying & printing.
What are the best copy protection solutions & strategies to protect research data from leakage, theft and misuse and how to securely share data.
There are many solutions you can use to protect research data from being accessed by unauthorized users, but only some prevent unauthorized activity such as copying or altering of content. Some solutions say they can prevent editing or printing, but those controls are easy to bypass or remove. Other systems only work within certain boundaries. Here we examine the security solutions available to protect research data from theft and unauthorized disclosure and what copy protection software you can use to prevent authorized users from copying, sharing and changing content.
 How to protect research data securely
How to protect research data securely
When we think of digital theft, it’s often intellectual property or customer data that springs to mind. Researchers within the scientific community, however, will know that stolen research data can be just as valuable and damaging. Whether it’s how studies are conducted or the results themselves, research is the lifeblood of the healthcare, technology, and academic industries. The documents and reports created as a part of this process must be well-protected if a project is to succeed. The unfortunate reality, however, is that key documents must be passed around for analysis and review, in some cases with outside partners. For that, you need a solution that enables you to share documents securely with external parties.
Strategies to protect research data

To prevent the leak of research documents, organizations must start with culture. To process data securely, organizations have to establish clear access rules, organized in a way that delivers the best possible control, and carefully vet any third parties. Those who process or otherwise utilize research data should additionally receive information security or cybersecurity awareness training so they can better spot spear-phishing attempts and other attacks.
Keeping employees trained and aware of the procedure creates a so-called ‘human firewall’. Any attacker trying to extract information or credentials will have to overcome research contributors’ instincts and training to be successful. However, it doesn’t protect against purposeful insider or third-party leaks, which can come with a significant financial incentive. To fully protect their research data, organizations need to employ the necessary technical measures (software solutions) to prevent unauthorized access.
There are many ways you can protect research data but not all of these solutions, however, are effective. Here are the most common and best ways to protect research data from sharing, theft and misuse.
 Protecting research data with encryption and passwords
Protecting research data with encryption and passwords
Encryption is a popular way of protecting documents from unauthorized access, especially PDF files, but the method used to authenticate and decrypt the files is vital. Password protecting a PDF with Adobe, for example, has many pitfalls.
Firstly, passwords are only as strong as the characters and the number of characters you use in them. Insecure or weak passwords can be cracked in seconds or minutes by a variety of freely available tools. If you use the same password to access all of your documents, you have a large security flaw. However, if you use a different password for each, it will quickly become unwieldy since you need to remember, manage and distribute them to others.
Passwords also do not help to protect against insiders or third-parties with malicious intent. Once the recipient of a document has a password, they’re free to share it, and the document, with anyone who might want to view it. Or they can just remove it and share the unprotected PDF file with others.

Encrypting a PDF with a password using Adobe Acrobat
So, we have established that using a password to protect research data may only be effective if you trust the recipient not to give your documents to other people.
 Certificate encryption
Certificate encryption
A more secure approach to research data sharing would be to use certificates to encrypt PDF documents since you don’t have to worry about distributing passwords securely. However, they come with their own problems which is discussed here: is it best to encrypt a PDF with a password or certificate?
 PDF restrictions or permissions to stop editing, copying, printing
PDF restrictions or permissions to stop editing, copying, printing
Assuming you trust authorized users not to share research data with others, most likely you will want to stop editing to prevent modification of information. Or you may want to disable printing to stop hard copies being misplaced or unknowingly distributed.
A common way to prevent alteration of research data is to convert a file to PDF and then disable editing by using Adobe Acrobat permissions or restrictions. You can use any PDF editor to do this, by selecting the option to prevent editing and setting a permissions password to prevent this control from being removed.
In practise however not all PDF readers obey these permissions (they just ignore them), and users can also easily remove them in seconds using free online PDF password removal tools – see removing PDF passwords. In other words they are completely useless and don’t stop users altering or printing content.
So if you want to prevent editing of your research data DON’T bother applying PDF permissions to do so – they are completely ineffective.
 Securing Research Data with Access Control & DLP systems
Securing Research Data with Access Control & DLP systems
 Microsoft’s Active Directory
Microsoft’s Active Directory
One alternative recommended by the European University Institute is an Access Control system, the most popular being Microsoft’s Active Directory. Such a solution can be very effective in preventing unauthorized access and on-premises unauthorized sharing. A set of databases and services connect users in the organization with only the resources they need, at the specific time period they need them, and restrict everything else. However, controls are set at the user or group level rather than the document level.
 Active Directory Rights Management Services
Active Directory Rights Management Services
However, traditional Access Control solutions don’t properly support sharing with outside parties, a step that’s often crucial in research. Though documents can be encrypted with technology like Active Directory Rights Management Services, this protection doesn’t extend past the external network and is often limited to Windows devices. Also, the document controls are rather limited:

Active Directory Rights Management
- Read – users can read a document but not edit or print it
- Change – users can read, edit, and save changes, but not print it
- Full control – users can do what they like with the document
There are also other drawbacks to the system:
- if you allow saving, users can save documents to other file formats
- if you allow printing, users can print to unprotected PDF files
- users can use screen grabbing software to take high quality screenshots
As such, it’s not usually sufficient on its own.
 Azure Active Directory
Azure Active Directory
Microsoft’s cloud-based rights management solution, Azure Active Directory, is a better choice since it provides more flexible controls.

Azure Active Directory Rights Management
Though it too isn’t designed for third-party sharing, it’s not too difficult to add an outside party. However, it requires the time-consuming and expensive setup of document classification and access policies, and its protection is still limited outside of Microsoft’s ecosystem.
You also have to consider that you have to upload unprotected research documents to the cloud (to a hosted Azure system unless you host it yourself) where they could be compromised if a system has not been adequately protected.
 Data Loss Prevention systems
Data Loss Prevention systems
Data Loss Prevention systems can also be a very helpful tool to prevent information leakage. By scanning data transferred via email, instant messaging services, and on cloud storage solutions, or USB, they can stop data from exiting an organization. Pre-defined rules may allow only authorized users to decrypt a document or stop users from copying a document to a USB stick.

WatchGuard Technologies DLP system
They do however have a few downsides:
- they aren’t the best for secure third-party document sharing, as they encrypt documents as soon as they leave the network and their encryption key systems don’t typically allow them to be decrypted.
- they are rather complex to setup and manage.
- they don’t enforce any document controls such as restricting editing or printing.
 | How to keep research data confidential – stop unauthorized access & prevent changes with document DRM |
Every researcher will have heard of Occam’s razor, and will have frustratingly run into its popular inaccurate paraphrase: “the simplest solution is almost always the best”. In the case of research, this is often a damaging statement, but when it comes to protecting research data, it may just be correct.
Protected document with dynamic watermark in Safeguard Secure PDF Viewer
Document DRM solutions are relatively simple but can effectively cut down leaks and unauthorized sharing. They encrypt a document and then provide a variety of controls to control how those documents can be used, such as:
- Which users and organizations can view, edit, or print a document
- How many times they can view or print it
- Where they can view it from, based on location data and IP address
- Remote access revoking
- Tracking and logging
- Automatically expiring access after a defined period of time or uses
- Dynamic watermarks to identify users
By applying these controls without relying on passwords, organizations retain full control over how their documents are distributed while retaining the ability to share securely with third parties. Utilizing DRM in combination with cloud-based screening tools, training, and other security solutions greatly reduces the chance of vital research data leaking. They can also ensure you comply with GDPR – General Data Protection Regulation and HIPPA regulations.
A WORD OF WARNING: make sure the PDF DRM solution does not force users to remove or lower their security for it to work. Some PDF DRM solutions force users to enable JavaScript in their PDF Reader (used by hackers to tack control of a system), or disable security controls for their plugin to work. Bear in mind that Browser based DRM systems also provide weak security – they are easy to bypass with users either sharing login details or removing the JavaScript protection in the browser. For an example of how insecure JavaScript-based browser controls are, see how easy it is to bypass Google Docs security.
 How to protect research data securely with copy protection
How to protect research data securely with copy protection
If you want to share research data securely with others then Locklizard is the best way to protect research data since it provides additional copy protection over Azure Rights Management with device locking, IP locking, screenshot protection, dynamic watermarks, flexible expiry options and more.
Locklizard enables you to protect research data from copying, being altered, stolen or compromised by using encryption and DRM controls to prevent unauthorized access and control how data can be used.
There are no complex systems or policies to setup and manage. Rather than using passwords or certificates, we use a licensing control system that provides transparent and secure key management. There are no passwords for users to enter or certificates for you to manage. Only authorized users can access research data, and documents are locked to authorized user’s devices so they cannot be shared. If a protected document is copied to another device it will fail to open.

Locklizard provides a full range of DRM and copy protection controls to stop theft, sharing and unauthorized disclosure of research documents:
Our PDF copy protection software automatically enables you to:
- Prevent changes – restrict PDF editing and modifying
- Block copying and copy/paste
- Disable PDF printing
- Stop screenshots by preventing the use of screen grabbing software
- Expire PDF files automatically on a specific date, after a number of days use or opens
- Lock PDF files to devices and locations
- Prevent saving to unprotected formats
- Add dynamic watermarks that cannot be removed
- Secure PDF forms – stop form fields from being changed and form data altered after submission
- Track PDF opens and prints
- Revoke access instantly at any time
Locklizard enables you to securely share and distribute research data without fear of it being accessed by unauthorized users or abused by authorized users.
One of the most important features of a PDF DRM system is locking PDF files to devices so they cannot be easily shared with others. Combined with transparent key delivery, this can provide the ultimate in protection for your sensitive research materials.
 | How to protect research data, articles, papers & documents with Safeguard PDF Security |
Safeguard PDF Security is also simple to use. You protect research documents on your computer (so unprotected documents never leave your control) and you distribute them just like any other file.
- Right-click on a PDF on your computer and select ‘Make Secure PDF’.
%22%20transform%3D%22translate(1%201)%20scale(2.11719)%22%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20cx%3D%22224%22%20cy%3D%221%22%20rx%3D%22133%22%20ry%3D%2229%22%2F%3E%3Cellipse%20cx%3D%22244%22%20rx%3D%22138%22%20ry%3D%2230%22%2F%3E%3Cellipse%20cx%3D%2224%22%20cy%3D%223%22%20rx%3D%2229%22%20ry%3D%2216%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Creating a protected PDF file
- Select the copy protection controls you want to apply. Note that by default, editing, copying, and printing are disabled.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%235194ca%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(508.06451%20-1.40545%20.14966%2054.10264%20291.4%205.5)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-306.52329%20137.1145%20-92.6746%20-207.17664%20296.5%20351.9)%22%2F%3E%3Cellipse%20fill%3D%22%23d5d2cf%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(172.3%20177.7%20320.7)%20scale(483.63947%2056.22878)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Encrypting a PDF without passwords or certificates using Locklizard Safeguard PDF DRM
- Press the Publish button to protect the PDF.
- Select the users you want to give access to your protected PDF files using the cloud-based Admin System:
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%2355c4df%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(90.2%20107.3%20141)%20scale(43.64149%20572.09553)%22%2F%3E%3Cpath%20fill%3D%22%23fffffe%22%20fill-opacity%3D%22.5%22%20d%3D%22M-73.4%20560.4l-79.9-346%20412.5-95.2%2079.8%20346z%22%2F%3E%3Cellipse%20fill%3D%22%23d8d2d1%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-12.04925%20-60.99846%20128.61015%20-25.40483%20192%20305.4)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Safeguard Admin System
- Then distribute the protected PDF just like any other file.
 FAQs
FAQs
Does encryption protect research data from unauthorized access?
Yes, but only when the data is encrypted. Once an authorized user has decrypted it they can give the decrypted version to others.
Does encryption adequately protect research data?
No, it only protects data in storage or transit. If you want to share research data securely with others then you need to use a rights management solution (IRM, ERM, DRM) to enforce copy protection controls to prevent editing, copying, printing and sharing.
Do PDF restrictions or permissions stop copying, editing, printing?
No. Permissions or restrictions added with a PDF editor (editing, copying and printing restrictions) and protected with a password are totally useless.
Some PDF readers completely ignore the restrictions and users can use free password removal or recovery software to remove the restrictions in seconds.
Can you protect research data from change?
Yes, but only if you use a rights management system such as DRM (Digital Rights Management), IRM (Information Rights Management) or ERM (Enterprise Rights Management) to enforce copy protection. All rights management systems differ in the level of functionality that they provide.
Does Azure Active Directory prevent screenshots of document content?
No. Users can use screen capture tools to take high-quality screenshots.
Some screen grabbing tools can automate screen capture and uploading, so it can be a quick way to copy document content.
Does Azure Active Directory prevent printing to PDF if printing is allowed?
No. If you allow users to print they can print to unprotected PDF files.
What is the best way to protect research data, articles, papers and documents?
With Locklizard PDF DRM copy protection software. Whether you want to protect medical data, clinical data, market research data, graduate research data, hippa protected research data or other documents from leakage and theft, Locklizard will protect against unuathorized access and stop authorized users from sharing, copying, editing and printing content.
If you want to protect research data from unauthorized access, sharing, editing and printing then take a free 15 day trial of our PDF DRM software.

 How to protect research data securely
How to protect research data securely Protecting research data with encryption and passwords
Protecting research data with encryption and passwords Certificate encryption
Certificate encryption PDF restrictions or permissions to stop editing, copying, printing
PDF restrictions or permissions to stop editing, copying, printing Securing Research Data with Access Control & DLP systems
Securing Research Data with Access Control & DLP systems Microsoft’s Active Directory
Microsoft’s Active Directory Active Directory Rights Management Services
Active Directory Rights Management Services Azure Active Directory
Azure Active Directory Data Loss Prevention systems
Data Loss Prevention systems How to protect research data securely with copy protection
How to protect research data securely with copy protection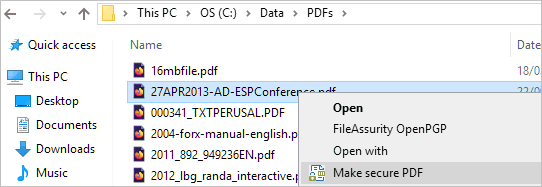


 FAQs
FAQs