Secure file sharing, FTP, email & document sharing

The pros and cons of different file sharing methods & how to share documents securely
The limitations of FTP, email, and secure file & document sharing services and how DRM can help protect sensitive documents.
What’s the best way to securely share files & documents?
Though there are countless ways to share files online, the most common tools in a professional context are secure file sharing sites, secure document sharing sites, and FTP. However, despite their prevalence, there is a significant amount of confusion surrounding how these systems work, the functionality they offer, and the security they provide for confidential and sensitive data. Here we cover the solutions available and the best way for businesses to securely share documents and files.

 Secure file sharing with FTP
Secure file sharing with FTP
The File Transfer Protocol (FTP) is an old but standard protocol used to transfer files over the internet from a server to a client PC. Its ability to allow the easy modification of files on a remote PC has made it a favorite with website or server admins, who can view and interact with the entire folder structure.
Is FTP secure?
Though it has its uses, FTP is not very secure and not very intuitive for non-technical users. To transfer files via FTP, you must download an FTP client application such as FileZilla or CyberDuck and enter the hostname, port, and other FTP credentials.

These credentials also form the basis of a major security flaw in FTP – its reliance on clear-text usernames and passwords for authentication and lack of encryption of files being transferred. A user on the same network can quite easily sniff network traffic to uncover FTP credentials, intercept file information, or perform a man-in-the-middle attack.
SFTP (SSH File Transfer Protocol) fixes these issues, encrypting data transfers and allowing for stronger forms of authentication such as SSH keys. However, it still does not give the admin any control over how files are used. Users are free to copy, print, edit, or share them as the files are downloaded to their local PC. Additionally, there is little to stop an authorized user from sharing their login info with somebody else.
 Secure file sharing sites
Secure file sharing sites

Secure file sharing sites such as Dropbox, SmartVault, etc. are one of the most popular ways to share files within an enterprise, and it’s easy to see why. They require no deployment and seemingly allow users to upload a file or folder to a single cloud service to receive comprehensive security and access from any device.
Unfortunately, the security of these online file services is usually just marketing nonsense. While they make a big deal about your files being encrypted when in transit and at rest, this is the minimum you should expect from any cloud service. Meanwhile, the “security” is just a set of basic access controls. You can control whether users can edit, delete, or create a file…and that’s it. There’s usually no control over what a user does beyond that. Further, these controls are enforced with JavaScript and are therefore easy to bypass. They won’t prevent a PDF file from being downloaded, or any other file for that matter.
There are other concerns with such services, too:
- you are uploading unprotected files to servers that are not under your control and you can’t personally verify the security of
- you do not know if temporary cleartext files are left over on the server after the files are encrypted
- secure links to files are just password protected
- Users can just share their login credentials / 2FA with somebody else
While you may find them acceptable for non-sensitive files, we cannot recommend using them for ones that contain sensitive or confidential information. They’re best used if you want to share files with a lower risk of interception.
Of course, you could use Google Drive, Microsoft OneDrive, Google Doc share, or Apple iCloud for file sharing, but their main purpose is to store files and sync them to your computer and for backup.
 Secure document sharing & collaboration services
Secure document sharing & collaboration services
Secure document sharing solutions differ from secure file sharing sites in that they enable users to view documents online in a controlled manner – i.e. users cannot edit, copy, print, download files, etc.
 Secure document collaboration
Secure document collaboration

When it comes to secure document sharing, cloud collaboration services such as Google Docs, Adobe Experience Manager document security, Azure cloud security, etc. are heavily promoted across dozens of media outlets. If you don’t know how they work, this is the basic setup:
- you upload documents to your account on the cloud service or create them on there
- these files are (hopefully) encrypted when they are not in use
- you can then share the documents with others and decide whether they can edit and print, or just view
- the browser enforces these options via JavaScript, disabling the print button, copy and paste, and editing functionality
There are various problems with this approach, chief among them being the use of JavaScript to enforce the controls. The problem with JavaScript is that it executes partially on the user’s local PC via the browser. This means that the printing and copy/paste controls can usually be bypassed quite easily by either disabling JavaScript or modifying it using the browser’s developer tools. Though this might sound complicated, you can read Google Docs Security to see just how easy it is. Once this has been achieved, users can copy the contents to another document or print without issue.
Another problem is that there is no reliable way for browsers to prevent screenshots or screen recordings. Though there have been attempts to prevent this by streaming services, they can easily be bypassed by turning off hardware acceleration. Even in the ideal scenario, where you are sharing with a non-technical user, they can just share their account to grant access to the documents shared with them.
Of course, cloud collaboration services also have the same pitfall as general file sharing ones: unencrypted files on an infrastructure not under your control.
 Secure document sharing rooms or virtual data rooms
Secure document sharing rooms or virtual data rooms
Secure data rooms are just another form of cloud-based document sharing sites. They let you add a collection of documents to a secure server and grant users the ability to view them in the browser when they log in using a username and password. They were initially created for the finance industry for M&A transactions.
Protection here is usually better than secure file sharing and collaboration sites as the ability to edit does not need to be maintained. Documents are usually converted to images to maintain support for multiple file types. This presents some usability issues, such as slow rendering and poor performance, but does make it impossible to edit or copy and paste through traditional means.
However, it is still far from bulletproof:
- Print prevention can usually be bypassed to create shareable copies and enable the bypassing of expiry dates.
- Users can still screenshot the document, and if they can screenshot it then they can run it through an OCR tool and make it editable.
- Failing this, they can just share their login credentials.
- If you want users to be able to download files for offline use, often you can’t do so without losing all protection.
Ultimately secure document sharing sites might be fine for M&A, where both parties have a vested interest in documents not leaking. They aren’t, however, suitable for the sale of documents or for selling ebooks, training courses, etc., and are not ideal for use cases where you do not have full trust in the other party.
 Email encryption & secure file sharing
Email encryption & secure file sharing

One popular way to share a file securely is to send it by email.
There are many secure email apps such as Hushmail, Protonmail, etc. that can protect messages and email attachments with end-to-end encryption. You can also add a plug-in to Outlook and other email clients that will encrypt emails before sending them.
While confidential mode in Gmail is marketed as a secure way to send emails, it does not provide end-to-end encryption or protect attachments. In addition, restrictions can be easily bypassed.
The main issue however with sending files securely by email is the max file size limitation – it is usually 25MB.
If you want secure file sharing for business and need to transfer large files, then it is best to use a file sharing site instead. Be aware however that they may not be as secure as you think. Using SharePoint for external sharing for example, does not prevent authorized users sharing files with unauthorized ones.
 | Locklizard: the best way for businesses to securely share documents |

Locklizard PDF DRM is a more secure alternative to the above solutions for secure document sharing. It moves away from flawed browser-based security and instead uses a combination of strong encryption, transparent licensing, and a secure viewer application.
Using Locklizard to protect PDF files securely is quick and simple. Admins protect a PDF file using Safeguard Writer and then add their intended recipients as users in their admin portal. The system will automatically send them an email with the license file and a link to the Safeguard Reader application required to open the document. The protected PDF document can then be delivered however you like, as only authorized users can open it.
How to share documents securely:
- Right-click on a PDF on your desktop and select ‘Make Secure PDF’.
%22%20transform%3D%22translate(1%201)%20scale(2.11719)%22%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%3E%3Cellipse%20cx%3D%22224%22%20cy%3D%221%22%20rx%3D%22133%22%20ry%3D%2229%22%2F%3E%3Cellipse%20cx%3D%22244%22%20rx%3D%22138%22%20ry%3D%2230%22%2F%3E%3Cellipse%20cx%3D%2224%22%20cy%3D%223%22%20rx%3D%2229%22%20ry%3D%2216%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Creating a protected PDF file
- Select the copy protection controls you want to apply. By default, editing, copying, and printing are disabled.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%235194ca%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(508.06451%20-1.40545%20.14966%2054.10264%20291.4%205.5)%22%2F%3E%3Cellipse%20fill%3D%22%23fff%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-306.52329%20137.1145%20-92.6746%20-207.17664%20296.5%20351.9)%22%2F%3E%3Cellipse%20fill%3D%22%23d5d2cf%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(172.3%20177.7%20320.7)%20scale(483.63947%2056.22878)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Encrypting a PDF without passwords using Safeguard PDF DRM
- Press the Publish button to protect the PDF.
- Add a user account and send them their license via the Safeguard admin portal. See how to add a new user and grant them document access.
%27%20fill-opacity%3D%27.5%27%3E%3Cellipse%20fill%3D%22%2355c4df%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22rotate(90.2%20107.3%20141)%20scale(43.64149%20572.09553)%22%2F%3E%3Cpath%20fill%3D%22%23fffffe%22%20fill-opacity%3D%22.5%22%20d%3D%22M-73.4%20560.4l-79.9-346%20412.5-95.2%2079.8%20346z%22%2F%3E%3Cellipse%20fill%3D%22%23d8d2d1%22%20fill-opacity%3D%22.5%22%20rx%3D%221%22%20ry%3D%221%22%20transform%3D%22matrix(-12.04925%20-60.99846%20128.61015%20-25.40483%20192%20305.4)%22%2F%3E%3C%2Fg%3E%3C%2Fsvg%3E)
Safeguard Admin System
- Distribute your protected PDF document just like any other file. A protected PDF can only be opened by somebody who is authorized to view it. Nobody will be able to edit, copy and paste, or save it and you will have chosen whether they can screenshot or print it.
For a more detailed look at the process, you can read our full guide on how to add security to a PDF.
 Document DRM Security features that prevent sharing
Document DRM Security features that prevent sharing
Once your PDF file has been encrypted, users will be unable to bypass its protections. There are no passwords to be shared, and decryption keys are locked to the device that the license file is activated on. Additionally, content is only ever decrypted in memory and the Viewer application has sufficient control over the operating system to block all routes to bypass print or editing controls.
In addition to the security features already mentioned, you can:
- lock devices to locations and IP addresses
- prevent printing or limit prints to a certain number & quality
- add dynamic watermarks that identify the reader
- expire documents based on opens, prints, date, or days since open
- revoke user or document access regardless of where the document is stored
- integrate our APIs for automatic document protection, user & document management
- access real-time stats for document usage
Despite this security, organizations do not need to give up their existing cloud storage or file sharing subscriptions. Locklizard-protected PDFs can be distributed via any method, including a public-facing website, as only those with authorization will be able to view them.
Take a 15-day free trial of our DRM software to see how Locklizard secure document sharing can work for you.
 FAQs
FAQs

How does a secure file-sharing service differ from secure document sharing?
Secure file-sharing services enable users and businesses to share files (via a link or login to a portal) that are downloaded to their devices for use offline. Files can also be accessed via a mobile app. While they are meant to be used for sharing files securely with team members, they can also be used for file storage purposes. Access controls are used to restrict access to specific files and folders. Once downloaded, users have full control over the files and can freely share them.
Secure document sharing services enable users and businesses to share files (via a link or login to a portal) which are then accessed and viewed online in a web-browser. Access controls are used to restrict file access, and DRM controls or restrictions are used to prevent copying, editing, printing, etc. Some even use the more secure attributed based access controls (ABAC), which take context into account. In theory, users cannot freely share documents due to the restrictions added to them, but browser-based systems provide limited protection. Printing and copy-paste controls are typically easy to remove.
How secure is Google Drive documents share?
It offers the same security as Google Docs – which is to say not much at all. It only takes a minute to remove copy and paste and printing controls and screenshots are never prevented. Additionally, users can just share their account details with others.
Are Box documents secure to share?
Box is a browser tool and does not provide effective controls to prevent copy and pasting, printing, screenshots, etc. Additionally, employees have a tendency to share files on the service using public links that anybody who knows the URL can access.
So, Box documents are only secure to share if you trust the person you are sending them to, you are following best practices, all of your users’ accounts are secure, and the server they are stored on is secure. There are too many variables here for this to be suitable for sensitive and confidential documents or for documents you sell.
Are documents shared in Dropbox secure?
Dropbox offers the same level of security as other secure file sharing sites. It only allows you to control who has access, whether they can edit, when the document expires, and whether downloads are allowed. However, because it does not prevent printing, screenshots, or copy and pasting, users who are authorized to view the document can easily share it with others, edit it in a new file, and more.
For the best protection for shared Dropbox files, protect them using a PDF DRM solution first.
Is secure file share phishing common?
Secure file share phishing has become increasingly common since the pandemic. With so many companies utilizing secure file sharing services, it is fruitful for attackers to send targeted emails to employees asking them to log in to view a document on their secure file sharing service of choice. Of course, users are directed to a fake login page, where their information is captured and used to extract sensitive information from the real file sharing service.
This is another reason why services that rely on usernames and passwords or the web browser in general are flawed.
Is FTP transfer secure?
No. In fact, it is very insecure. FTP transfers are not encrypted, which means that anybody spying on your traffic can see the files you are sending and your FTP credentials. SFTP transfers do use encryption and are a better alternative, but they have no control over what happens after a user downloads a file.
How do users view Locklizard secure PDF documents?
Users install a Viewer app on their desktop (Windows & Mac) or mobile device (iOS & Android) or they can access files in a browser. Once they have received their license file by email, they click to activate it. They can then view any secure documents you have authorized for them to access.
Why are passwords not the best way to securely share documents?
Password protection has many failings. The main one being is that users can share passwords with others. In terms of data security, a strong password may not be easily cracked, but if the object is to prevent authorized users from sharing your files then they provide little in the way of protection. If you need secure file sharing for business and want to prevent sharing and copying, then only DRM can achieve this.
What is the safest way to share confidential documents?
The safest way to share or send confidential and sensitive documents is to protect them using DRM software first. You can then prevent unauthorized sharing, copying, editing, printing, etc. If you just encrypt a document you have no control over it once it has been decrypted – so users can share it freely with others.
Which is better, cloud-based or on-premise for sharing files securely?
They both provide the same security controls and sharing options but have their own advantages and disadvantages.
Cloud-based: you have to upload unprotected files to someone else’s server where they may be compromised. You are usually locked into monthly pricing. The sharing service however is available straight-away and you do not have to maintain a server.
On-premise: you have full control over your unprotected files. Perpetual licenses may be available making it a lot cheaper. You have to configure and maintain a server.
Are there other ways a business can share files securely?
Yes, we have not mentioned a VPN (Virtual Private Network), peer-to-peer solutions, or distribution via a USB device. These can all be used as a free secure file-sharing platform but are beyond the scope of this blog.

 Secure file sharing with FTP
Secure file sharing with FTP Secure file sharing sites
Secure file sharing sites Secure document sharing & collaboration services
Secure document sharing & collaboration services Secure document collaboration
Secure document collaboration Secure document sharing rooms or virtual data rooms
Secure document sharing rooms or virtual data rooms Email encryption & secure file sharing
Email encryption & secure file sharing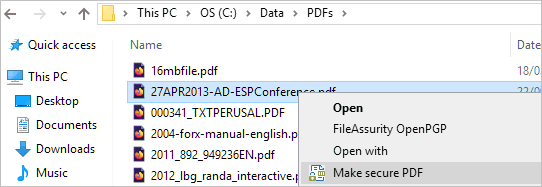


 Document DRM Security features that prevent sharing
Document DRM Security features that prevent sharing FAQs
FAQs